
Introduction
Several alternatives, ranging from open-source to commercial, are available for remote desktop solutions.
After testing various options, I’ve used RustDesk in my infrastructure for quite some time. While the open-source version served me well, I recently explored RustDesk Server Pro, which offers additional enterprise-grade features. Both solutions have proven to be reliable and robust.
While tools like Apache Guacamole, TigerVNC, and others offer similar capabilities, I chose RustDesk for its stability, straightforward setup process, and flexibility in choosing between self-hosted open-source and commercial solutions.
RustDesk Server Pro is the commercial sibling of the open-source version, offering enhanced capabilities like:
- Enterprise-level security features
- Priority support
- Advanced user management
- Commercial license
This guide will show how to install a RustDesk Server Pro on Hetzner Cloud.
For RustDesk Server Pro pricing details, you can look at the official pricing page.
This guide follows the official documentation from:
- Docker installation and some shortcuts
- Docker post-installation
- RustDesk Server Pro self-hosting
- My configuration related to the Nginx Proxy Manager
Article Roadmap
Here’s what we’ll cover step-by-step:
- Hardware Requirements
- Creating the Server on Hetzner
- Connecting to the VM
- Configure Docker ecosystem
- Domain and DNS Prep
- Configuring Reverse Proxy: Nginx Proxy Manager vs. Direct Nginx Setup
- Reverse Proxy Setup
- RustDesk Server Pro Core
- Network Security with Firewall
- Client Configuration
- First login to RustDesk Console
Hardware Requirements for RustDesk Server Pro
RustDesk Server Pro is designed to be resource-efficient, making it possible to run even on modest server configurations. Below are the recommended specifications:
- Basic VPS Server: A low-tier VPS configuration is sufficient for most use cases. The server software is not CPU- or memory-intensive.
- Public Server Example: RustDesk’s public ID server, hosted on a Vultr server with 2 CPUs and 4GB RAM, supports over 1 million endpoints.
- Relay Connections: Each relay connection consumes approximately 180 kbps of bandwidth. A configuration with 1 CPU core and 1GB RAM is enough to support 1,000 simultaneous relay connections.
These details indicate that even a server with minimal resources can run RustDesk Server Pro effectively, making it a scalable solution for small and large deployments.
Creating the Server on Hetzner
Environment Preparation
If you don’t already have a Hetzner Cloud account, you must create one by visiting https://hetzner.cloud/?ref=vJLpYsXw0BK6 and completing the registration process.
By using this referral link, you’ll receive €20 in Hetzner Cloud credits to get started!
Once you click the referral link, you’ll see a congratulations page confirming that you’ve received cloud credits. Click “Continue” to proceed with the registration process.
You’ll then be redirected to the main Hetzner Cloud page, where you can learn more about their services. To complete your account creation, click the red “Sign Up” button in the top-right corner and follow the registration steps.
After completing your registration, you can access the Hetzner Cloud console at https://console.hetzner.cloud/projects to start creating your first server.
Registered users can access the Hetzner Cloud console at https://console.hetzner.cloud/projects.
Once logged in:
- Click on “+ New project”
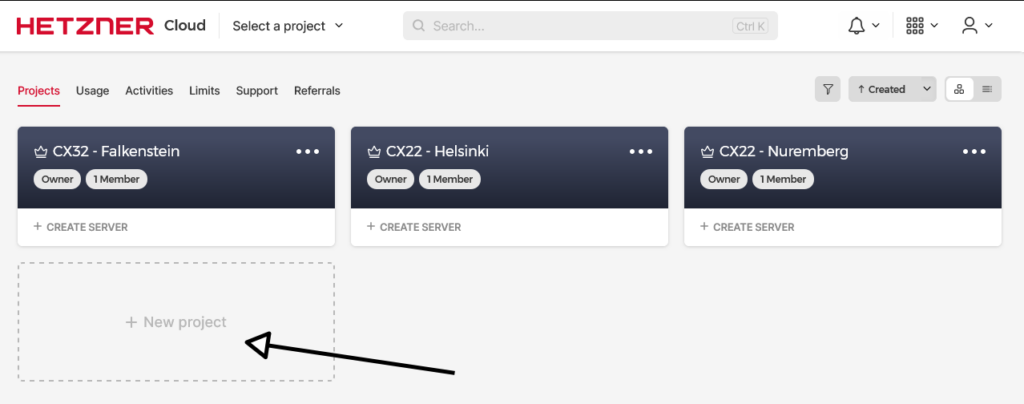
- Create a project named “RustDesk“
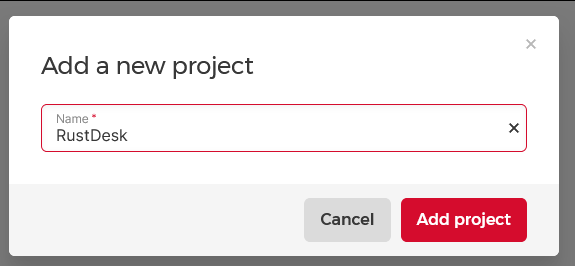
- Access the project and click the red “Create Resources” button followed by “Servers”
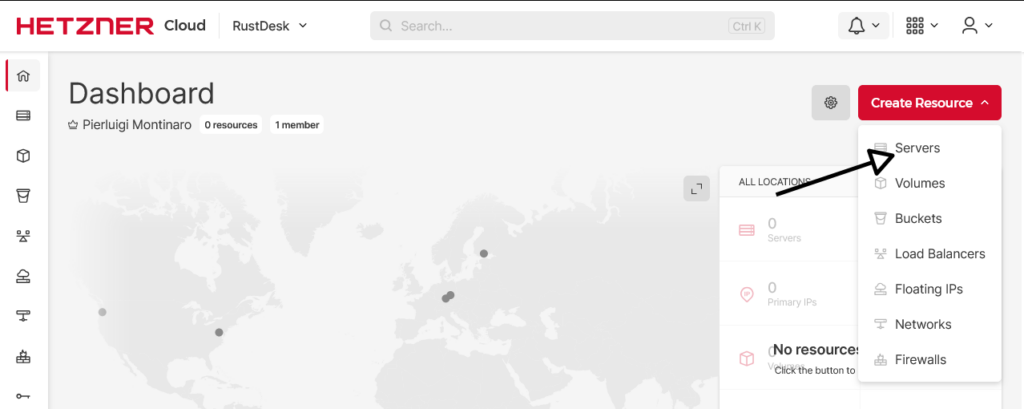
Server Configuration
- Location: Helsinki
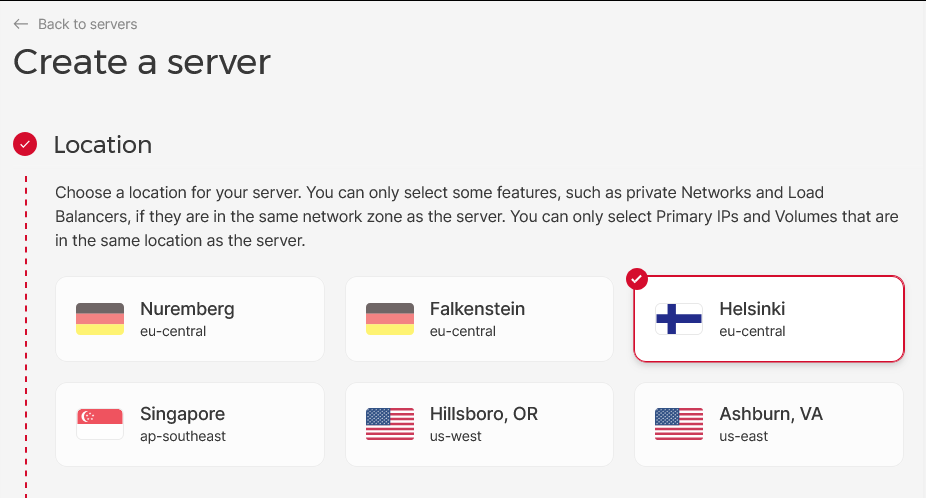
- Image: Ubuntu 24.04
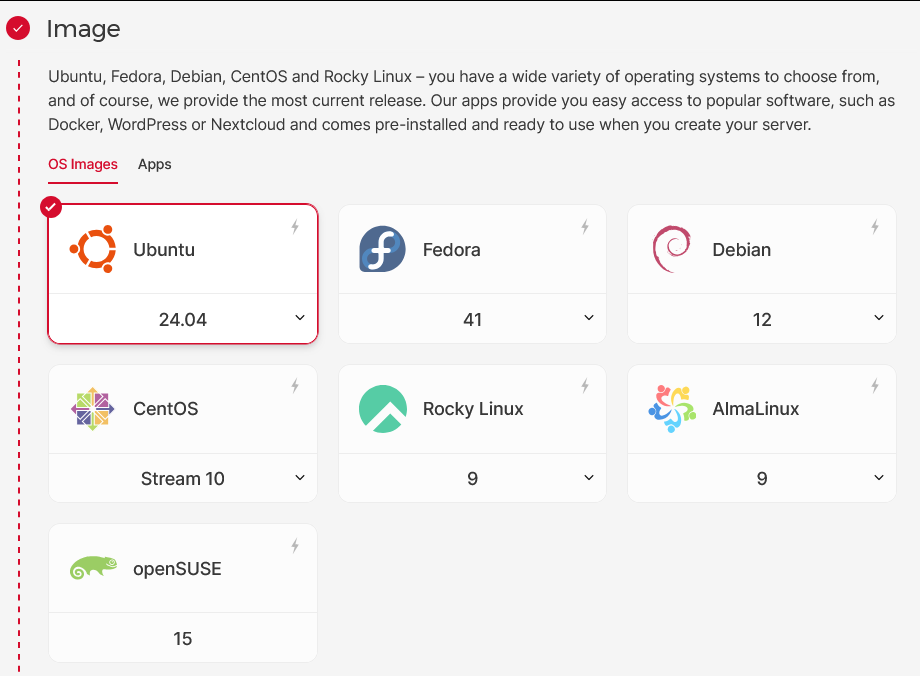
- Type: Shared vCPU (Architecture: x86 Intel/AMD)
- Server: CX22 (2 vCPUs, 4GB RAM, 40GB SSD)
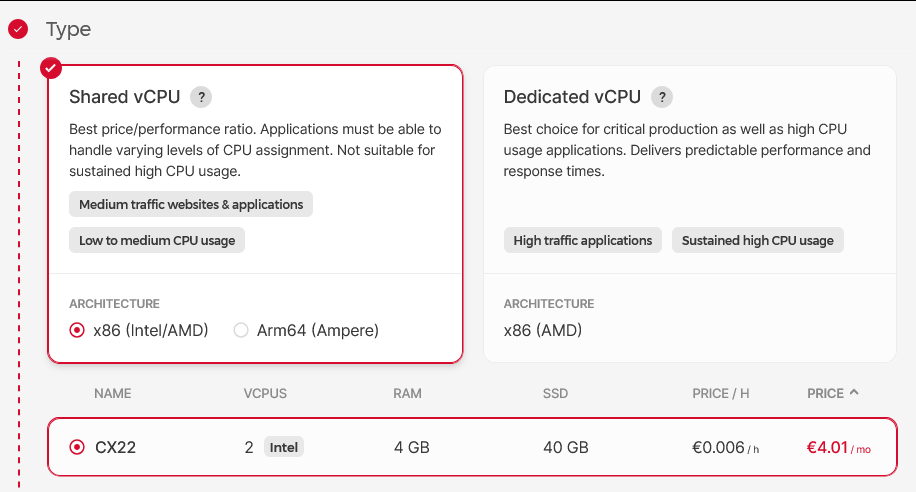
- Networking: leave default settings with public IPv4 and IPv6
- For the “SSH keys” section, we need to prepare the keys.
SSH Key Configuration
Security is paramount, so we’ll use an Ed25519 SSH key, which offers better security and efficiency compared to RSA and ECDSA.
Before proceeding on the Hetzner console, let’s generate our SSH key on our local Linux machine using the command:
ssh-keygen -t ed25519 -f ~/.ssh/id_ed25519_hetzner_rustdeskOn the Hetzner console, in the “SSH Keys” section:
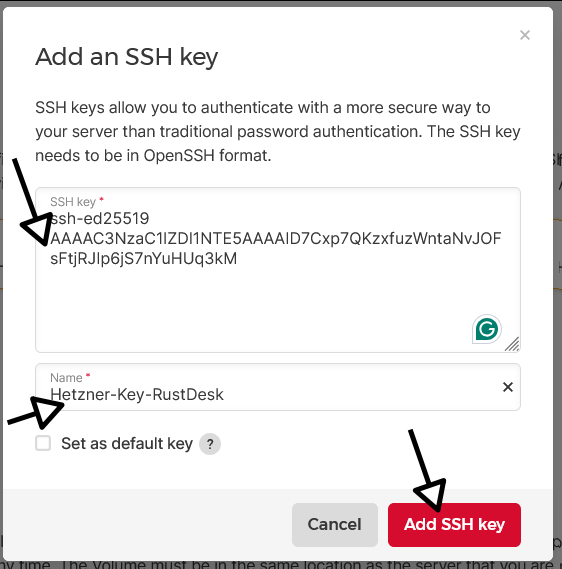
- Click on “+Add SSH key”
- Paste the contents of ~/.ssh/id_ed25519_hetzner_rustdesk.pub (the public key)
- Give your key a name (e.g., “Hetzner-Key-RustDesk“)
- Click on “Add SSH key”
Completing VM Configuration
For the remaining sections:
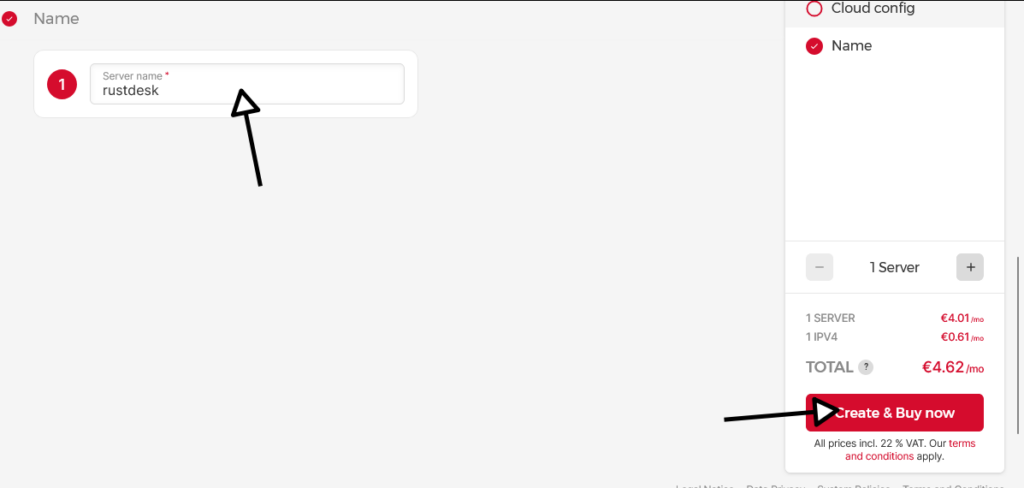
- Skip “Volumes”, “Firewalls”, “Backups”, “Placement groups”, “Labels”, and “Cloud config”
- Name the VM “rustdesk“
- Click the “Create & Buy now” button at the bottom right to create the VM
- Obtain your IP address after a few minutes
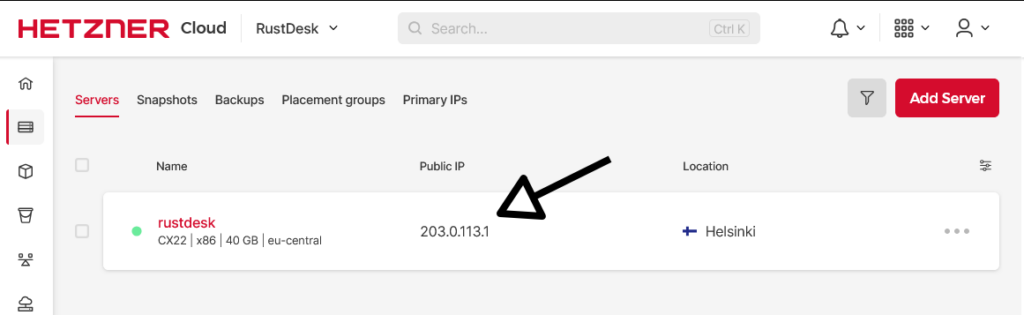
In my case, I got the IP address 203.0.113.1
Connecting to Your VM
Initial Root Connection
First, connect to your newly created VM as root:
ssh -i ~/.ssh/id_ed25519_hetzner_rustdesk root@203.0.113.1Creating a Non-Root User
For security best practices, it is recommended that a dedicated non-root user run Docker instances instead of using the root account. This enhances security by limiting privileges and reducing potential attack vectors.
Some cloud providers, such as Vultr, automatically create a non-root user (e.g., ubuntu, debian, or ec2-user). If your provider has already created a non-root user, you can use that user instead of creating a new one.
However, on Hetzner Cloud, there is no default non-root user, so we need to create one manually. This guide will create a user named rustdesk and configure passwordless sudo access.
# Create the rustdesk user
adduser --disabled-password --gecos "" rustdesk
# Add rustdesk user to sudo group
usermod -aG sudo rustdesk
# Set up SSH key authentication
mkdir -p /home/rustdesk/.ssh
cp /root/.ssh/authorized_keys /home/rustdesk/.ssh/authorized_keys
chown -R rustdesk:rustdesk /home/rustdesk/.ssh
chmod 700 /home/rustdesk/.ssh
chmod 600 /home/rustdesk/.ssh/authorized_keys
# Configure passwordless sudo for rustdesk user
echo "rustdesk ALL=(ALL) NOPASSWD:ALL" > /etc/sudoers.d/rustdesk
chmod 440 /etc/sudoers.d/rustdeskSwitching to Ubuntu User
Logout from the root session and reconnect as rustdesk user:
ssh -i ~/.ssh/id_ed25519_hetzner_rustdesk rustdesk@203.0.113.1System Preparation
Now that we’re connected as the rustdesk user, let’s proceed with Docker installation in the fastest way I know.
Docker Installation
Execute the following command to install Docker:
bash <(wget -qO- https://get.docker.com)User Configuration
To avoid using sudo for every Docker command, add your user to the docker group:
sudo usermod -aG docker $USERInstallation Verification
Log out and log back in to apply the group changes, then verify the installation with:
docker run hello-world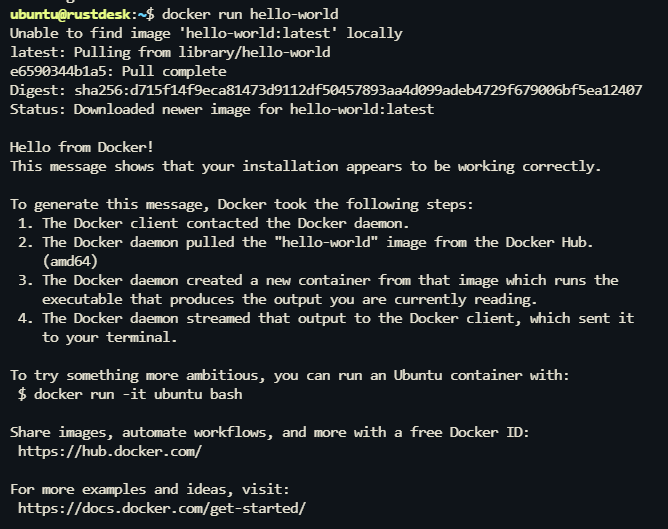
Domain and DNS
Configuring DNS Records in Cloudflare for RustDesk Server Pro
You’ll need to configure DNS records to access your RustDesk Server Pro via a custom domain.
Below, I’ll guide you through the process of setting up an A record and a CNAME record in Cloudflare. While this example uses Cloudflare, the steps are similar for other DNS providers.
Create an A Record
- Log in to your Cloudflare account and select your domain (e.g.,
montinaro.ovh). - Navigate to the DNS settings tab.
- Add a new record:
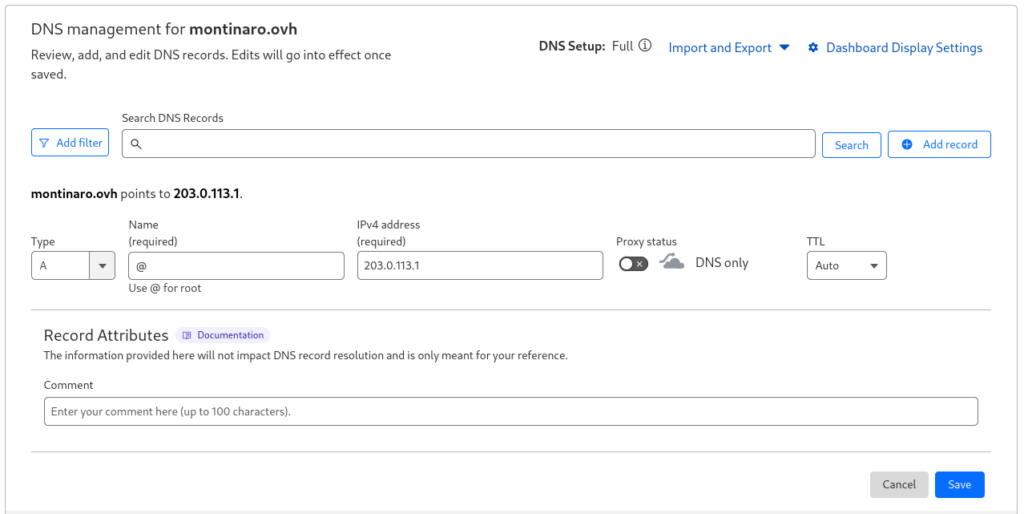
Fill the fields with the correct values, I’ll use:
- Type: A
- Name:
@(this represents the root domain, e.g.,montinaro.ovh) - IPv4 Address: Enter the public IP address of your server (e.g.,
203.0.113.1) - Proxy Status: Set to “DNS only” (gray cloud icon)
- Save the record clicking on “Save” button
Here’s how it should look once created:

Create a CNAME Record
- Still in the DNS settings tab, add another record:
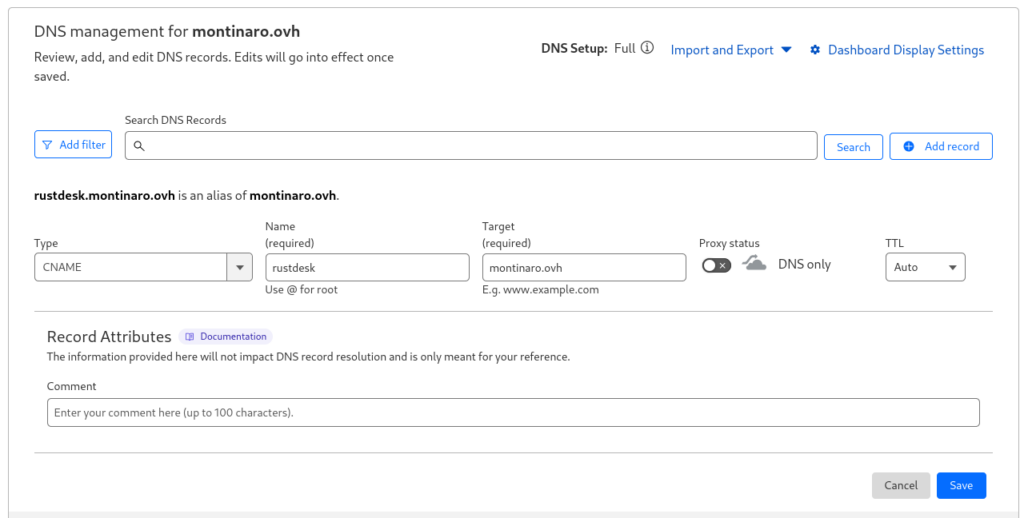
Fill the fields with the correct values, I’ll use:
- Type: CNAME
- Name:
rustdesk(this will createrustdesk.montinaro.ovh). - Target: Enter your root domain (
montinaro.ovh). - Proxy Status: Set to “DNS only” (gray cloud icon).
- Save the record clicking on “Save” button
Here’s how it should look after creation:
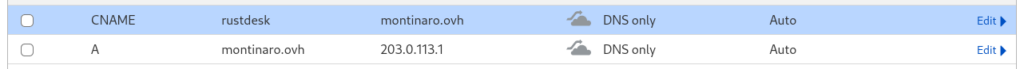
Why These Records?
- The A record points your root domain (
montinaro.ovh) to your server’s IP address. - The CNAME record creates a subdomain (
rustdesk.montinaro.ovh) that redirects traffic to the root domain.
Note for Other Providers
If you’re using a different DNS provider, the process is similar:
- Create an A record pointing to your server’s IP.
- Create a CNAME record for the subdomain pointing to the root domain.
Configuring Reverse Proxy: Nginx Proxy Manager vs. Direct Nginx Setup
To secure and efficiently manage web access to RustDesk Server Pro, I use Nginx Proxy Manager (NPM) as a reverse proxy. But why use NPM instead of configuring Nginx manually?
What is Nginx Proxy Manager?
Nginx Proxy Manager (NPM) is a user-friendly web interface for managing Nginx reverse proxy configurations. It simplifies setting up SSL certificates, handling multiple domain names, and configuring reverse proxy rules without requiring direct modifications to Nginx configuration files.
Why Use Nginx Proxy Manager Instead of Nginx Directly?
- Easy-to-use Web UI – No need to edit config files manually.
- Built-in SSL Management – Automatically request and renew Let’s Encrypt certificates.
- Simplified Proxy Rules – Quickly set up and manage multiple proxy hosts.
- Access Control & Logging – Additional security features like IP blocking and logging.
For those who prefer direct Nginx configuration, RustDesk provides manual HTTPS setup instructions in their documentation:
👉 Manual HTTPS Setup for Web Console
Nginx Proxy Manager Configuration
Preparing the Environment
First, create a dedicated directory for our Nginx Proxy Manager setup:
mkdir nginx-proxy-manager
cd nginx-proxy-managerCreating docker-compose.yml
Create and edit the Docker Compose configuration file:
nano docker-compose.ymlAdd the following content:
services:
app:
image: 'jc21/nginx-proxy-manager:latest'
container_name: nginx-proxy-manager
restart: always
environment:
PUID: 1000
PGID: 1000
DISABLE_IPV6: 'true'
ports:
- '80:80'
- '81:81'
- '443:443'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
healthcheck:
test: ["CMD", "/usr/bin/check-health"]
interval: 10s
timeout: 3s
deploy:
resources:
limits:
memory: 2G
reservations:
memory: 1G
networks:
- nginx_internal_network
networks:
nginx_internal_network:
name: nginx_internal_network
driver: bridgeRustDesk Configuration
Preparing the Environment
First, create a dedicated directory for our RustDesk setup:
mkdir rustdesk
cd rustdeskCreating docker-compose.yml
Create and edit the Docker Compose configuration file:
nano docker-compose.ymlAdd the following content:
services:
hbbs:
container_name: hbbs
image: rustdesk/rustdesk-server-pro:latest
command: hbbs
volumes:
- ./data:/root
network_mode: "host"
depends_on:
- hbbr
restart: always
hbbr:
container_name: hbbr
image: rustdesk/rustdesk-server-pro:latest
command: hbbr
volumes:
- ./data:/root
network_mode: "host"
restart: alwaysFirewall
Understanding Network Mode and Firewall
In our docker-compose.yml, we’re using network_mode: “host”, which means the containers will use the host’s network stack directly instead of Docker’s virtual networking.
This configuration provides better network performance, allows direct access to host network interfaces and bypasses Docker’s network virtualization.
However, even with host network mode, we still need to configure the host’s firewall (UFW) to allow incoming connections.
The firewall operates at the host level, regardless of how Docker is configured.
Firewall Configuration
Install and configure UFW (Uncomplicated Firewall):
sudo apt install ufw
# Allow SSH first to prevent being locked out
sudo ufw allow ssh
# Allow RustDesk required ports
sudo ufw allow 21114/tcp
sudo ufw allow 21115/tcp
sudo ufw allow 21116/tcp
sudo ufw allow 21116/udp
sudo ufw allow 21117/tcp
sudo ufw allow 21118/tcp
sudo ufw allow 21119/tcp
# Enable the firewall
sudo ufw enable
# Verify the configuration
sudo ufw statusThese ports are used for:
- 22 TCP: SSH access
- 21114 TCP: Web Console
- 21115 TCP: NAT type test
- 21116 TCP: TCP hole punching
- 21116 UDP: heartbeat/ID server
- 21117 TCP: relay
- 21118 TCP: support for web clients on Server
- 21119 TCP: support for web clients on Relay Server
Starting Nginx Proxy Manager service
Launch the Container
From the nginx-proxy-manager directory where we created the docker-compose.yml file, start the service and view the log:
docker compose up -d && docker compose logs -fThe -d flag runs the containers in detached mode (background), while logs -f allows us to monitor the logs in real-time.
Starting RustDesk Services
Launch the Containers
From the rustdesk directory where we created the docker-compose.yml file, start the services and view the logs:
docker compose up -d && docker compose logs -fThe -d flag runs the containers in detached mode (background), while logs -f allows us to monitor the logs in real-time.
Post-Launch Verification for RustDesk Server Pro
After launching the RustDesk services, Docker will create a data directory in your current folder. Inside this directory, you’ll find several files, but the most important one for client configuration is id_ed_25519.pub.
To view and save the public key:
# Display the content of the public key
cat data/id_ed25519.pub
# Save it to a separate file for backup
cat data/id_ed25519.pub > ~/rustdesk_public_key.txtImportant: This public key is crucial for secure client connections to your RustDesk server. Save it in a safe location, as you’ll need to configure it in every client that connects to your server.
Client Configuration
Download RustDesk Client
Visit https://rustdesk.com/download to see all available options and download the right client for your operating system.
Configure Client Settings
Once RustDesk is installed on your device:
- Open RustDesk
- Click on “Settings” in the top right of the screen
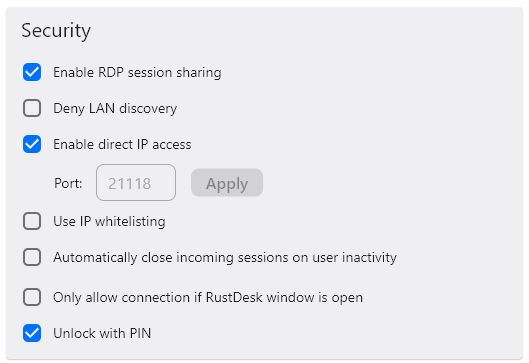
In the “Security” section:
- Click “Unlock security settings”
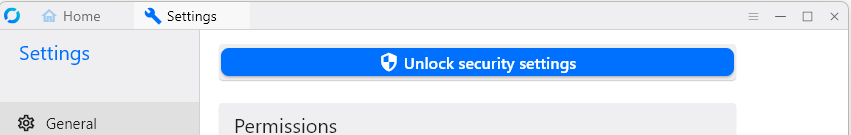
- Under “Password”, use “Set Permanent Password” if you need unattended access
- Set the one-time password length to 8 characters
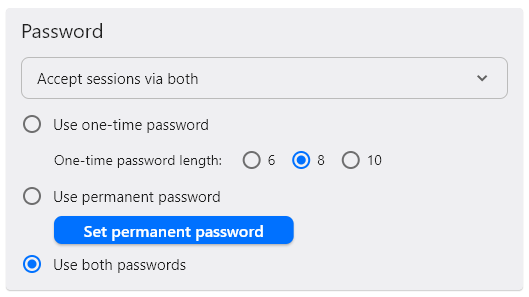
At the bottom, look for the “Security” block:
- Check “Enable direct IP access”
- Set the port to 21118 (default)
Configuring ID and Relay Server
When setting up RustDesk Server Pro, you need to configure the ID Server and, if necessary, the Relay Server.
If the ID Server (hbbs) and the Relay Server (hbbr) share the same IP address, you do not need to manually set the Relay Server.
RustDesk will automatically use the same IP for relay services.
You only need to specify the Relay Server if it runs on a different machine with a different IP or if you need specific settings. We’ll discuss this in a different article.
In the “Network” section:
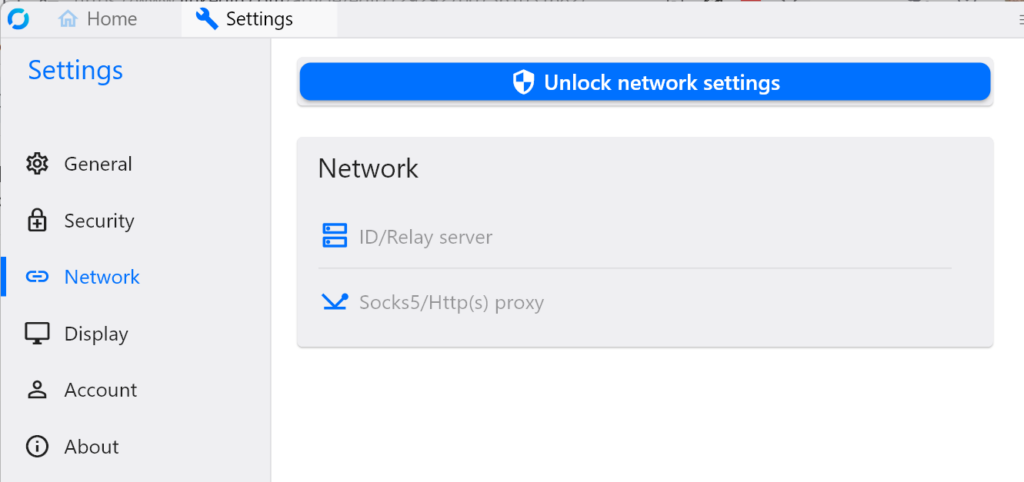
- Click “Unlock network settings”
- Click on “ID/Relay Server”
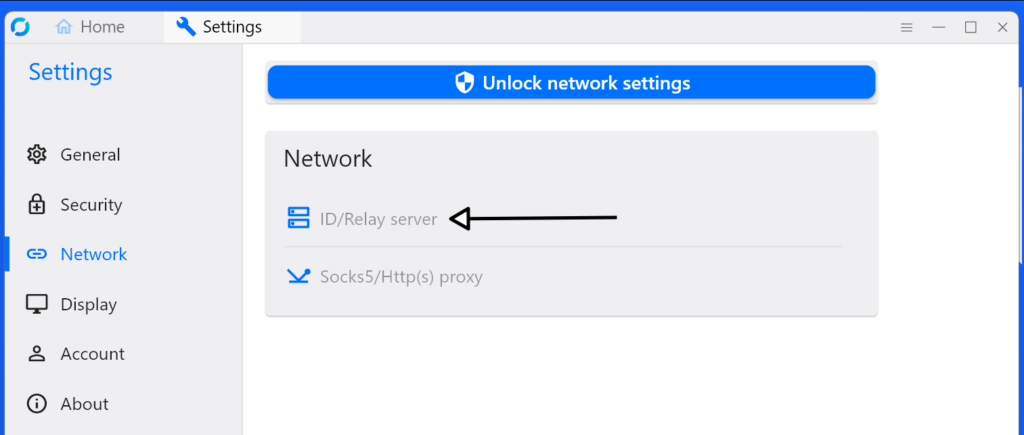
- Set the ID server address to: 203.0.113.1
- In the “Key” field, paste the content of data/id_ed25519.pub
Apply the changes, then navigate to the Home tab
At the bottom of the window, you should see the “Ready” message:
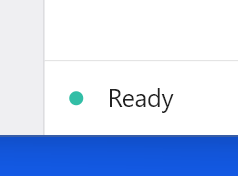
This indicates that your client is successfully connected to your self-hosted RustDesk Server Pro and ready to use.
You can use the RustDesk client with your RustDesk Server Pro to establish remote connections. However, this setup doesn’t yet leverage the platform’s full potential, such as accessing the RustDesk Console for advanced management and customization.
To unlock these features, you can follow the instructions below on configuring Nginx Proxy Manager to access the RustDesk Console securely via your custom domain.
Accessing Nginx Proxy Manager via the Browser
Accessing Nginx Proxy Manager via the Browser
Once Nginx Proxy Manager is running, you can access its web interface to configure your reverse proxy settings. Follow these steps:
Open the Admin Interface
- Open your browser and navigate to the following URL:
http://<SERVER-IP>:81; replace<SERVER-IP>with the public IP address of your server.
In my case, I’ll usehttp://203.0.113.1:81 - You will see the Nginx Proxy Manager login screen
- Use the default credentials to log in:
- Email: admin@example.com
- Password: changeme

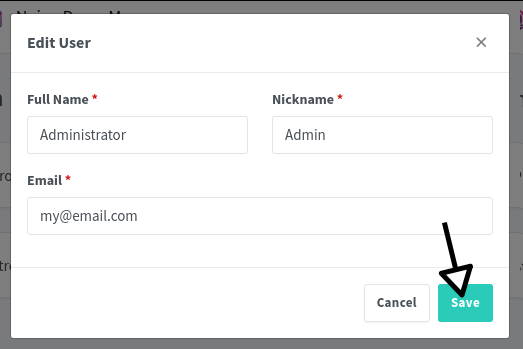
Update Admin Credentials
- After logging in, you will be prompted to update your credentials for security purposes.
- Enter a new Full Name, Nickname, and a valid Email Address in the fields provided.
- Save the changes by clicking the green Save button.
- Next, change the default password, navigating to the password change section.
- Enter your current password (
changeme) and set a new strong new password.
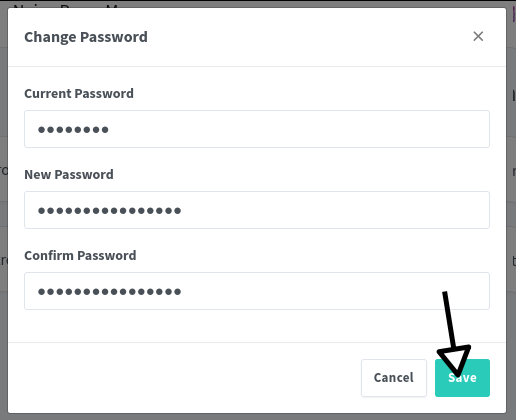
Ready to Configure Proxies
Now that you’ve secured your admin account, you’re ready to set up proxy hosts for RustDesk Server Pro.
Configuring a New Proxy Host in Nginx Proxy Manager
Now that you can access the Nginx Proxy Manager interface, it is time to create a new proxy host for your RustDesk Server Pro.
Navigate to Proxy Hosts
- From the Nginx Proxy Manager dashboard, click on “Hosts” in the top menu.
- Select “Proxy Hosts” from the dropdown. Navigate to Proxy Hosts.
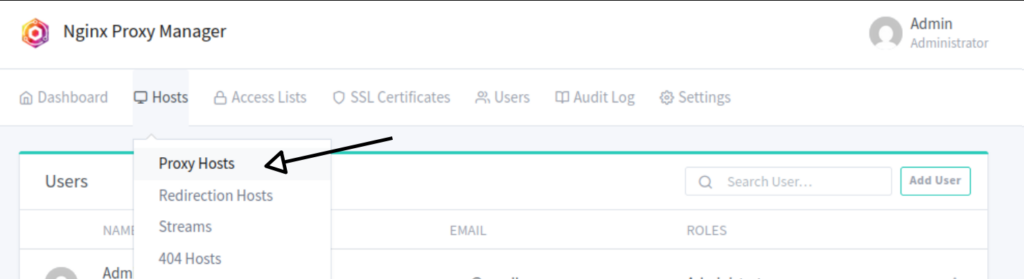
Add a New Proxy Host
- Click the green “Add Proxy Host” button.
- Fill in the following details under the Details tab:
- Domain Names: Enter your subdomain, I’ll use rustdesk.montinaro.ovh
- Scheme: Select
http. - Forward Hostname / IP: Enter your server’s private IP or public IP (e.g.,
203.0.113.1). - Forward Port: Enter the port where RustDesk Server Pro is running (e.g.,
21114). - Enable Websockets Support and Block Common Exploits.
- Leave “Access List” as “Publicly Accessible.”
- Your configuration should look like this:
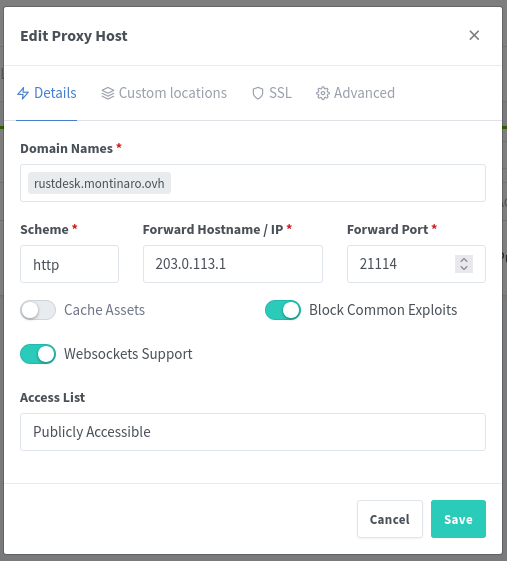
Configure SSL
- Click on SSL
- Select “Request a new SSL Certificate”.
- Enable:
- Force SSL
- HTTP/2 Support
- Enter your email address for Let’s Encrypt.
- Agree to the Let’s Encrypt Terms of Service.
- Click Save and wait for the SSL certificate to be issued.
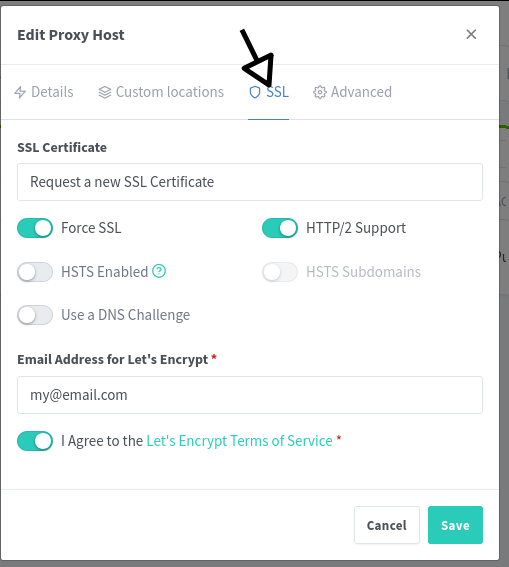
After a few seconds you’ll see something like this:
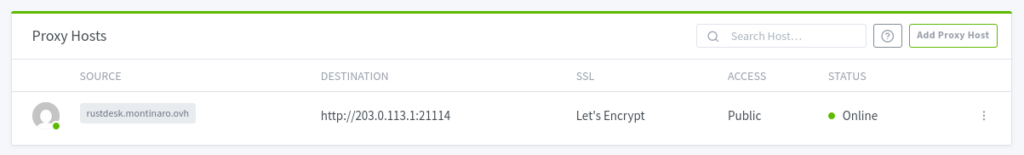
Connect to RustDesk Console
Once everything is configured, test your setup by navigating to your subdomain (e.g., https://rustdesk.montinaro.ovh). You should now see your RustDesk Server Pro interface accessible securely over HTTPS.
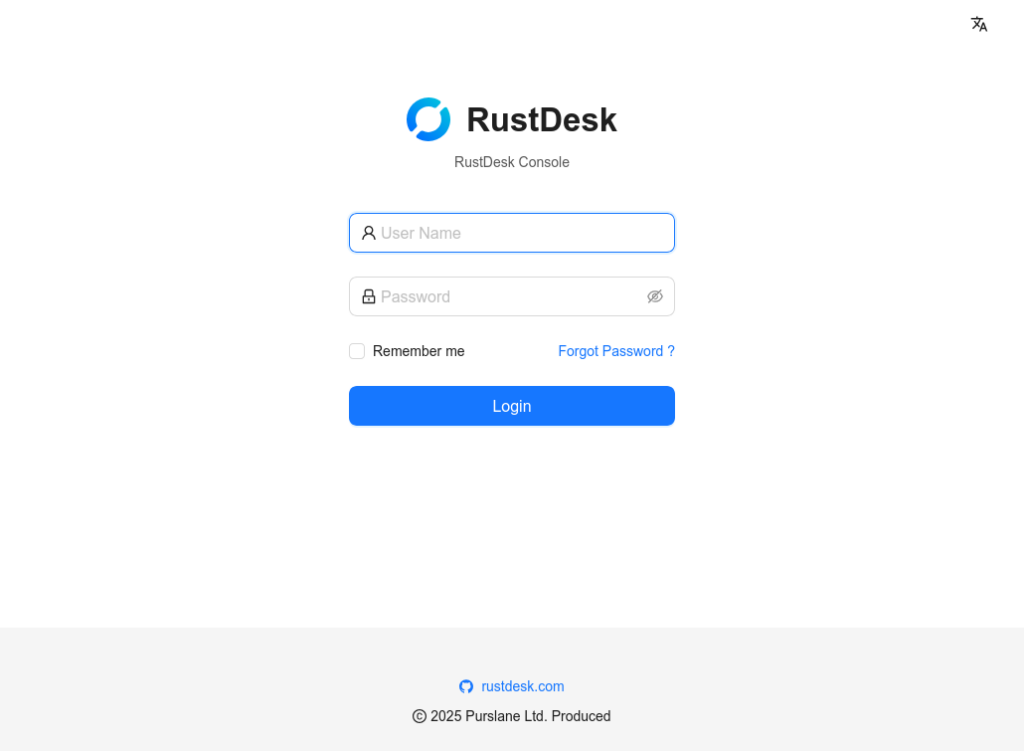
Login to the Console
- On the login page, enter the default credentials:
- Username:
admin - Password:
test1234
- Username:
- Click Login to proceed.

Enter Your License Key
- After logging in, you will see a notification stating that the license is not set.
- Enter your license key in the pop-up window and click OK to activate it.
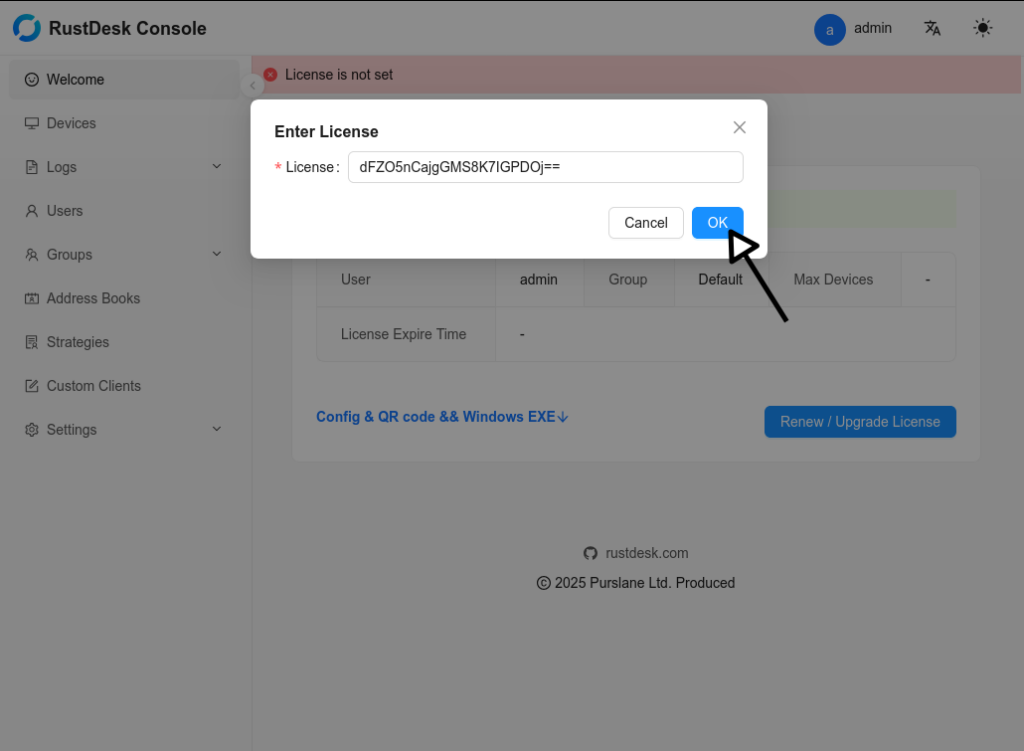
Enjoy the RustDesk Console
Once your license is activated, you’ll be redirected to the main dashboard. Here’s what you’ll see:
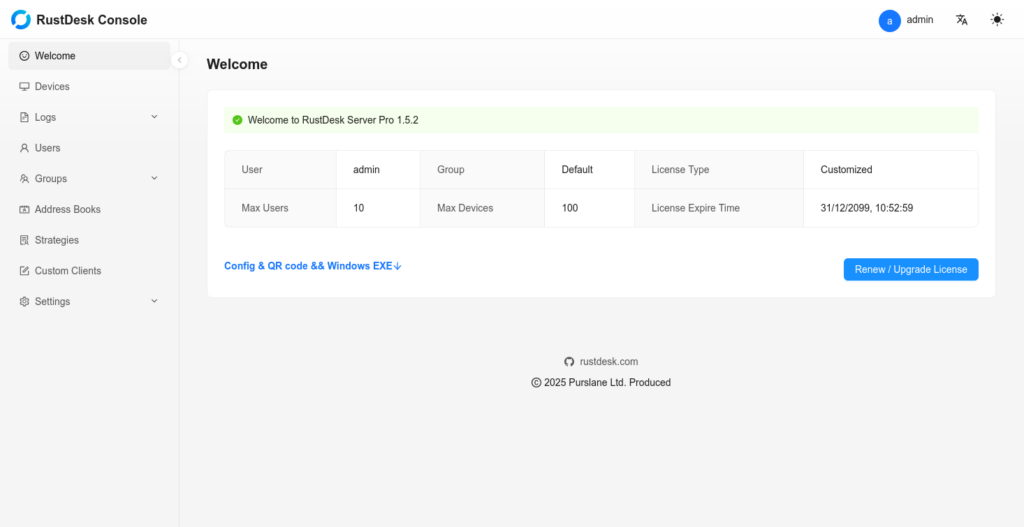
At this point, your RustDesk Server Pro is fully configured and ready forYour RustDesk Server Pro is fully configured and ready for secure remote access!
Another article will explore the capabilities of the RustDesk Console for RustDesk Server Pro.
Acknowledgments
I thank the RustDesk team for providing me with a Pro license to test and evaluate their solution. This generous support allowed me to explore the advanced features of RustDesk Server Pro and share my experience through this article.
Leave a Reply